In today’s digital landscape, cybersecurity has become a critical concern for organizations of all sizes. The rise of cyber threats such as malware, ransomware, and data breaches underscores the importance of implementing robust security measures to protect sensitive data and infrastructure. Wazuh is an open-source security platform that offers advanced threat detection, incident response, and compliance monitoring capabilities, empowering organizations to enhance their cybersecurity posture. In this comprehensive guide, we’ll explore the features, benefits, and applications of Wazuh, and examine why it has become a preferred choice for organizations seeking effective security solutions.
Wazuh is an open-source security platform that provides real-time threat detection, incident response, and compliance monitoring capabilities. Originally developed as an intrusion detection system (IDS), Wazuh has evolved into a comprehensive security solution that combines host-based intrusion detection (HIDS), log monitoring, vulnerability detection, and security analytics into a single platform. By integrating diverse security functionalities, Wazuh offers organizations a holistic approach to cybersecurity, enabling them to identify and mitigate threats before they escalate into full-blown security incidents.
Wazuh continuously monitors system and application logs, network traffic, and other sources of security telemetry to identify potential threats in real time. By analyzing log data for signs of suspicious activity, Wazuh can detect a wide range of security threats, including malware infections, unauthorized access attempts, and anomalous behavior indicative of a security breach. In addition to threat detection, Wazuh provides incident response and remediation capabilities to help organizations mitigate security incidents effectively. Through its integration with orchestration and automation tools, Wazuh enables security teams to automate response actions, such as quarantining compromised hosts, blocking malicious IP addresses, and initiating forensic investigations, reducing the time and effort required to contain and remediate security incidents.
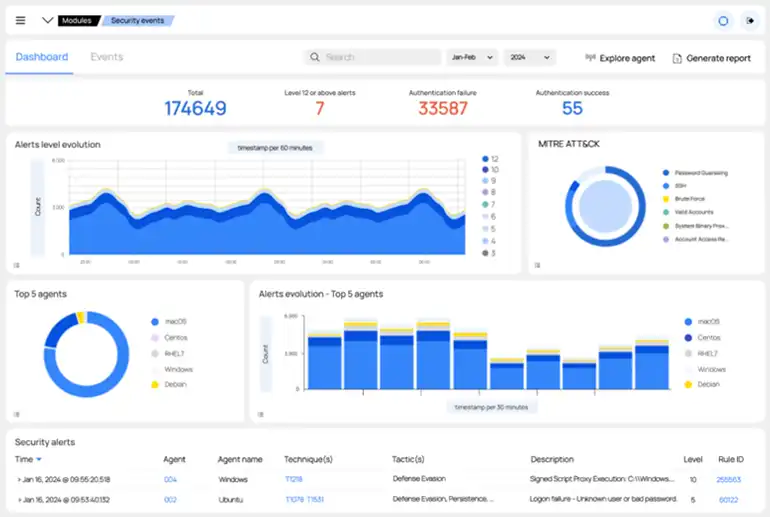
Wazuh offers robust log management and analysis capabilities, allowing organizations to centralize and analyze log data from across their IT infrastructure. By correlating log events and applying advanced analytics techniques, Wazuh helps organizations gain insights into their security posture, identify emerging threats, and prioritize response efforts based on the severity and impact of security events. Wazuh includes built-in vulnerability detection and compliance monitoring features to help organizations identify security vulnerabilities and ensure compliance with industry regulations and best practices. By scanning systems for known vulnerabilities, misconfigurations, and insecure applications, Wazuh helps organizations proactively address security risks and maintain a strong security posture.
Wazuh is designed to be highly scalable and flexible, making it suitable for organizations of all sizes and industries. Whether it’s a small business with a handful of endpoints or a large enterprise with a complex IT infrastructure, Wazuh can scale to meet the needs of any organization, providing comprehensive security coverage across diverse environments and use cases. Wazuh helps organizations enhance their threat detection and response capabilities by providing real-time visibility into security events and automating incident response actions. By detecting and responding to threats more effectively, organizations can reduce the risk of data breaches, minimize downtime, and protect sensitive information from unauthorized access.
By centralizing security monitoring and analysis, Wazuh enables organizations to gain a better understanding of their security posture and identify areas for improvement. Whether it’s strengthening access controls, patching vulnerabilities, or implementing security best practices, Wazuh helps organizations take proactive measures to enhance their overall security posture and reduce the likelihood of security incidents. As an open-source platform, Wazuh offers a cost-effective alternative to proprietary security solutions, allowing organizations to achieve enterprise-grade security capabilities without breaking the bank. By leveraging open-source technologies and community-driven development, Wazuh provides organizations with a high-quality security solution at a fraction of the cost of commercial alternatives.
Wazuh helps organizations achieve and maintain compliance with industry regulations and standards, such as GDPR, PCI DSS, HIPAA, and ISO 27001. By providing built-in compliance monitoring features and generating audit-ready reports, Wazuh simplifies the compliance process and helps organizations demonstrate adherence to regulatory requirements, reducing the risk of non-compliance penalties and fines. As an open-source project, Wazuh benefits from a vibrant community of users, developers, and contributors who collaborate to improve the platform and address security challenges. Whether it’s accessing documentation, participating in forums, or contributing code to the project, Wazuh users have access to a wealth of resources and expertise to help them maximize the value of their security investment.
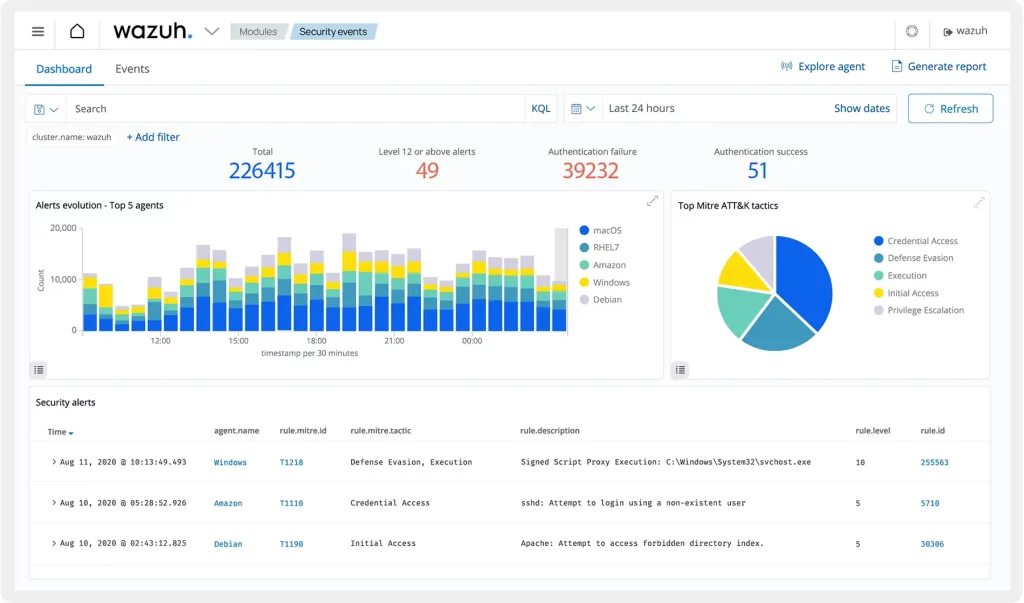
Wazuh is widely used for threat detection and incident response in a variety of industries, including finance, healthcare, retail, and government. By providing real-time visibility into security events and automating incident response actions, Wazuh helps organizations detect and mitigate threats quickly and effectively, minimizing the impact of security incidents on business operations. Wazuh is commonly deployed for log management and analysis, enabling organizations to centralize and analyze log data from servers, endpoints, network devices, and cloud environments. By correlating log events and applying advanced analytics techniques, Wazuh helps organizations gain insights into their security posture, identify suspicious activity, and respond to security incidents in a timely manner.
Wazuh is used for vulnerability management to help organizations identify and remediate security vulnerabilities in their IT infrastructure. By scanning systems for known vulnerabilities, misconfigurations, and insecure applications, Wazuh helps organizations prioritize patching efforts, reduce the risk of exploitation, and maintain a strong security posture. Wazuh is deployed for compliance monitoring and reporting to help organizations achieve and maintain compliance with industry regulations and standards. By providing built-in compliance monitoring features and generating audit-ready reports, Wazuh simplifies the compliance process and helps organizations demonstrate adherence to regulatory requirements.
Wazuh is increasingly being used for cloud security to help organizations protect their cloud environments from cyber threats and compliance violations. By integrating with cloud platforms such as AWS, Azure, and Google Cloud Platform, Wazuh provides visibility into cloud-based assets and helps organizations monitor for security events and compliance violations in real time.
Wazuh represents a powerful and versatile security platform that helps organizations enhance their cybersecurity posture through advanced threat detection, incident response, and compliance monitoring capabilities. By leveraging open-source technologies and community-driven development, Wazuh offers a cost-effective alternative to proprietary security solutions, empowering organizations of all sizes and industries to strengthen their defenses against cyber threats. Whether it’s detecting and responding to security incidents, managing logs and analyzing security telemetry, or achieving and maintaining compliance with industry regulations, Wazuh provides the tools and capabilities needed to protect sensitive data and infrastructure from evolving cyber threats. As cyber threats continue to evolve and grow in sophistication, Wazuh remains a trusted ally for organizations seeking to safeguard their digital assets and mitigate the risks of cyber attacks.





